Methodology Study
JTBD Framework
UX Researcher
✺
Research Manager
✺
2020 Dec~2023 Mar
✺

02 Personas with Purpose
Building Data- Driven Personas for Consumer and Corporate UX
00 Background
Back in the quiet weeks of December 2020, I finally had time to tackle something long overdue: rebuilding our consumer personas from the ground up. I paused all other research and created four new personas that better reflected our evolving user base, fully replacing the outdated set.
Fast forward two and a half years, and the corporate team was facing a similar need. But this time, we didn’t have the time or resources for a full-scale project. So instead, I led an iterative update as the UX Research Manager, guiding two researchers to refresh the existing personas using insights from recent studies.
Outdated or missing personas are a common challenge in UX research. In this case study, I’ll walk through how I approached both a full rebuild and a thoughtful revision—what worked, what I’d do differently, and lessons you might take into your next persona project.
Let’s begin with the consumer persona project: the ones built from scratch.
Note
I’ve included more detail than I typically would in a case study for fellow UXRs who might be looking for persona inspiration. I learned a lot from reading others and I’d love to give it back to the community.
Some of the extra content is folded by default and you can toggle it open to explore more.
Certain images have been intentionally blurred to respect confidentiality agreements.
Quick Jump
00
Background
01
Consumer Persona Reconstruct
02
Making the Case
03
Methodology Design
04
Research Execution
05
Synthesizing the Data
06
Key Findings
07
Impact
08
Reflection
✺
Consumer Persona Reconstruct
✺
01 Recognizing
the Problem
By late 2020, Malwarebytes was no longer just an anti-malware company. We had expanded into privacy protection with the launch of PrivacyVPN, and were in the process of shifting from license key activation to a more seamless, account-based management system, which not only simplifies the purchase flow, but also provides a better user experience for cross platfrom and multi-device usage.
While our products had evolved, our understanding of users had not. The existing consumer personas, created back in 2017, were outdated. They lacked behavioral depth, focused too heavily on buyers rather than users, and failed to reflect users' growing privacy concerns. As a result, the product, design, and marketing teams were operating without a shared, nuanced view of our customers.
Over time, the original personas had been reduced to caricatures: elastic, overly simplified archetypes that no longer served our decision-making needs.
“Jean-Luc – old and not tech-savvy”
“Ben – young and tech-savvy”
With fewer product launches scheduled for Q4 and newly promoted into the UX Research Manager role, I saw an opportunity to fix this. We needed a fresh, grounded, and scalable set of personas—ones that reflected real behaviors, motivations, and needs across our evolving user base.
02 Making the Case:
Proposal and Stakeholder Buy-In
What Was Broken
Confusion between personas and market segments
Across teams, personas had been reduced to oversimplified stereotypes—“Jean-Luc, old and not tech-savvy” and “Ben, young and tech-savvy.” While memorable, these elastic shorthand characters weren’t grounded in behavioral insight or product goals. They were malleable enough to support some argument but ultimately too vague to guide meaningful design.
No clear user motivations or goals
Scattered behavior patterns
Buyer and user roles were mixed together
Biased sampling
Privacy concerns were barely addressed
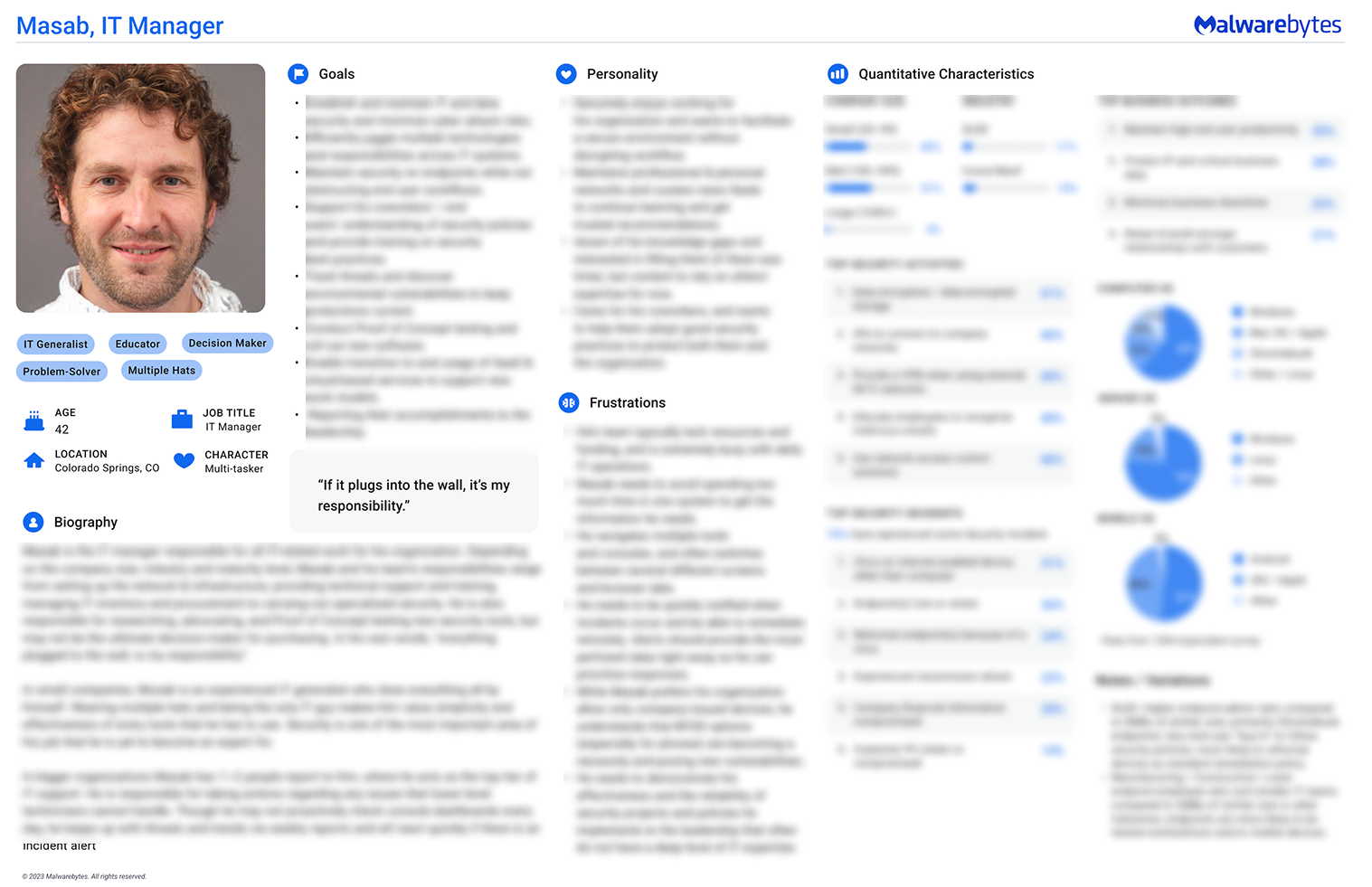
I can’t share the 2017 consumer persona example, but you can reference this corporate one. They were created using the same methodology and shared very similar structure.)
What I Would Do Differently
I proposed a hybrid persona framework, grounded in:
Goal-Directed Design (About Face: The Essentials of Interaction Design, by Cooper et al.)
Jobs-to-be-Done (JTBD) theory (When Coffee and Kale Compete, by Alan Klement.)
Ethnographic principles from applied anthropology
The new approach focused less on who users are, and more on what they’re trying to achieve—a better fit for product design and messaging.
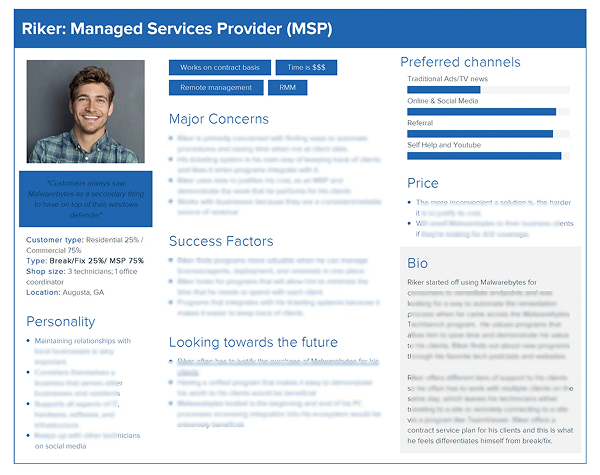
(A preview of the new persona format was shared with stakeholders to illustrate the value and usability of the updated approach.)
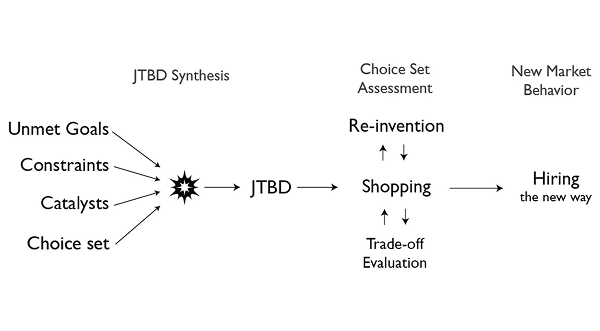
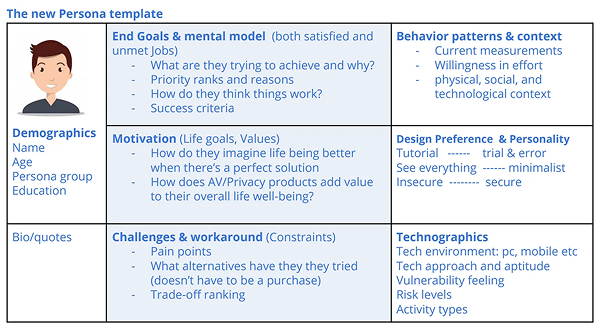
(The JTBD Data Model shows a process of how new market behavior is created. In this case, it shows how a JTBD is created and how it results in someone hiring solution(s) for it.)
A Clearer Communication Tool
Rather than updating old personas, I started from scratch. The new set would:
Highlight motivations and goals as the centerpiece
Distill clear behavior patterns, not demographic generalizations
Offer practical guidance for design, product, marketing strategies
Result: Stakeholder Buy-In
With strong cross-functional alignment, I dedicated 90% of my time to this foundational initiative while continuing to oversee enterprise research efforts.
Key Research Objectives
Rebuild personas from the ground up
Center on user motivations, goals, and behavior patterns
Deprioritize demographics and buyer-side data
Set the stage for Phase 2: Journey mapping (not covered in this case study)
✺
Planning the Approach
✺
With stakeholder buy-in secured, I moved into the execution of this project. Most of the My goal was to build a persona system grounded in rigorous theory, adaptable across product lifecycles, and usable by cross-functional teams.
03 Methodology Design
The research approach was deliberately layered and collaborative:
1.
Literature Review
Assessed modern persona frameworks, focusing on their application in tech and behavior-driven design.
2.
Product Audit & Heuristic Review
Mapped the current user experience across our consumer product suite to identify behavioral cues and UI gaps.
3.
Stakeholder Interviews
Aligned with cross-functional partners to understand business priorities and clarify scope boundaries.
4.
Iterative Plan Feedback
Presented early drafts of the research plan to design and PM leads, incorporating their feedback to ensure alignment.
5.
Recruitment & Interviews
Conducted remote 1:1 interviews with a diverse set of users, including non-customers, to avoid brand bias.
6.
Analysis & Persona Construction
Synthesized behavioral patterns, underlying goals, and job drivers into actionable personas.
Theoretical Foundations
TL;DR
It’s less about Who they are, and more about how they interact with our product and what they are trying to achieve and most importantly, why does it matter to them.
Theories and principles
This project was guided by a mix of Goal-Directed Design and Jobs-to-be-Done theories, with influences from cognitive psychology and anthropology. These frameworks helped me ask sharper questions, spot behavioral patterns in context, and build personas that were both practical and forward-looking.
Read More
04 Research Execution
Total Participants
46 (U.S. and Canada)
Interview Format
90-minute, 1:1 remote moderated sessions
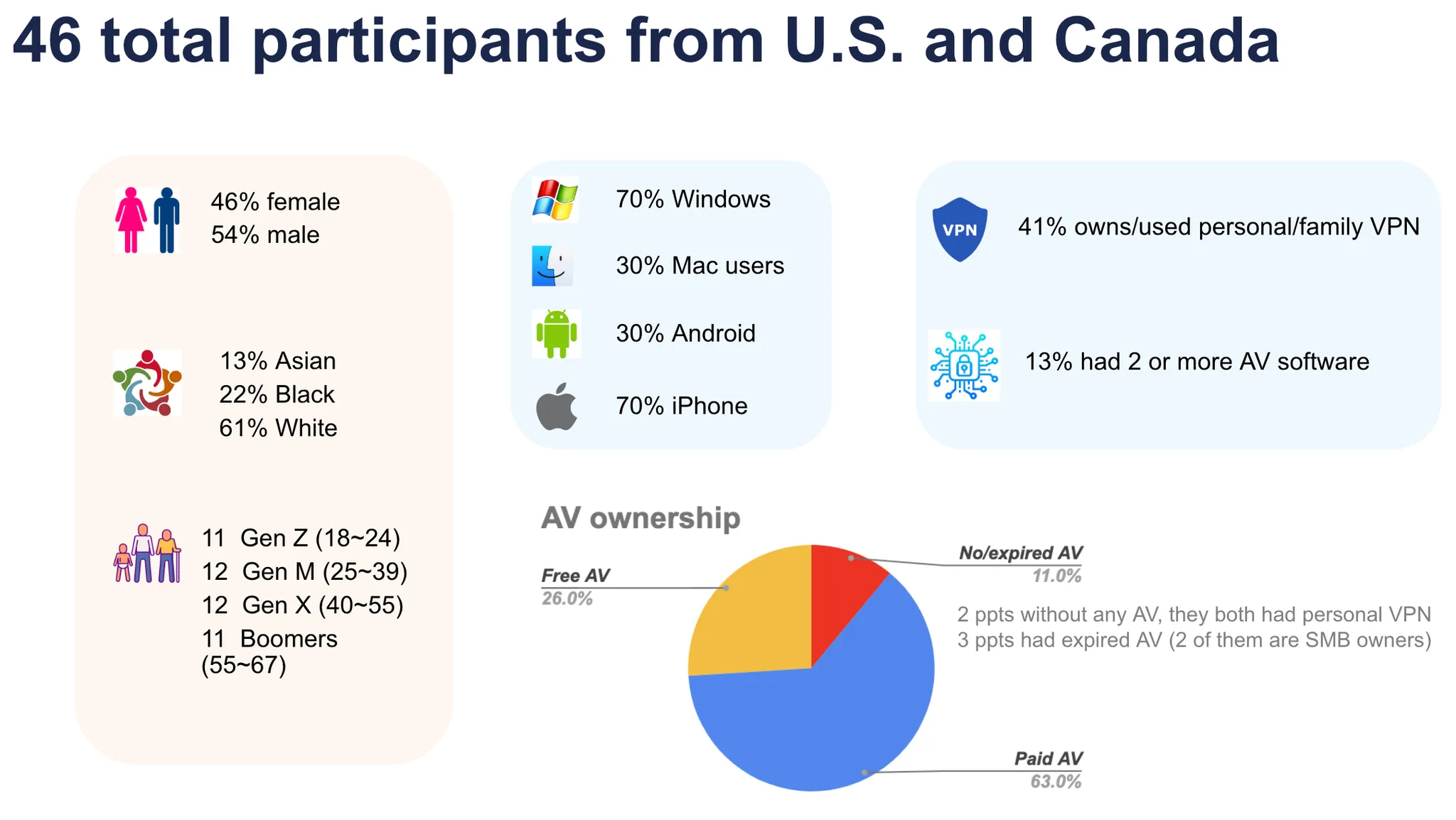
Interview Design
Each session combined open-ended narrative exploration with a few quantitative prompts to assess:
Security and privacy priorities
Confidence and vulnerability levels
Success criteria for digital security
The core focus was to understand the goals users were trying to achieve, their perceived constraints, and how they navigated their digital lives.
Research Question Guide
1. User Goals & Motivations:
What are they trying to achieve, and why?
2. Behavioral Patterns & Mental Models:
How are they currently navigating digital security?
3. Priorities & Trade-Offs:
How do they rank and justify their preferences?
4. Context of Their Digital Life:What life context shapes their decisions?
05 Synthesizing the Data
A total of 46 sessions were transcribed, coded, and analyzed across four key dimensions:
User goals – What they were trying to achieve
Behavioral patterns – How they approached protection and trade-offs
Mental models – What they believed would keep them safe
Contextual factors – Life stage, device sharing, past experiences
Iterative Clustering
Instead of fitting users into pre-defined archetypes, I took a bottom-up clustering approach to identify groups with shared patterns.
I experimented with different grouping methods—starting with goals, then behaviors, and vice versa—to stress-test the consistency of those patterns.
To supplement the qualitative clusters, I explored basic clustering algorithms using the small-scale quantitative data collected (e.g. vulnerability scores, confidence levels, security vs privacy priorities). Unsurprisingly, the sample size was too small to yield statistically significant clusters, but the data still served as a helpful validation layer to reinforce and challenge the qualitative segmentation.
Common protection goals
Similar logic around trade-offs (free vs paid, simplicity vs control)
Comparable levels of digital confidence and risk tolerance

(snapshot of early analysis: color-coded themes, initial categorization and frequency counts.)
Constructing the Persona Set
The final result was a set of five personas, each anchored by:
A core goal or mental model driving their decisions
A clear set of behavioral tendencies and trade-offs
Emotional and functional success criteria guiding their product expectations
Where relevant, I included overlapping buyer behaviors to support marketing and support team alignment, while ensuring the personas remained focused on in-product user needs.
✺
Key Findings & Personas
✺
06 Key Findings
✺
Security is shifting from device-first to human-first.
Users are thinking less about protecting devices and more about protecting themselves and their families.
✺
Privacy concerns are rising—but confidence remains low.
While users are increasingly aware of privacy risks, many feel ill-equipped to manage them.
✺
Desire for simplicity, transparency, and integration.
All-in-one tools are appealing—but only if they’re easy to use and clearly communicate what’s happening behind the scenes.
✺
Password managers are common but misunderstood.
Many rely on them daily, yet few fully understand how they work—or trust them completely.
✺
Brand trust is fragile.
Loyalty is not guaranteed; users expect ongoing relevance and clear value to stick around.
Quantitative Highlights
1.
89% of participants prioritized identity theft protection as a top need.
2.
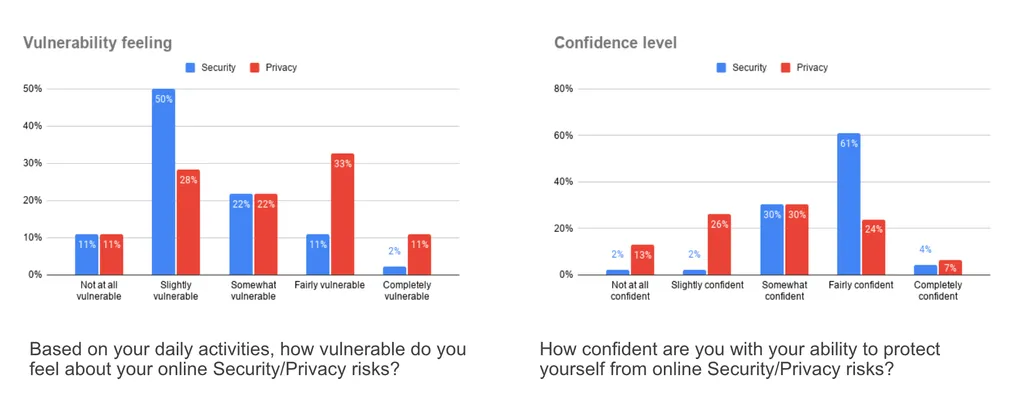
Privacy vulnerability was significantly higher than security vulnerability:
44% felt fairly or completely vulnerable about privacy risks (vs. 13% for security).
3.
Confidence in managing privacy was markedly lower than security:
Only 31% felt fairly or completely confident in managing privacy risks, compared to 65% for security.

Final Personas
Vesper
The Vulnerable Senior
The Petersons
Protective Parents (treated as a joint decision-making unit)
Issac
The Informed Power User
Priscilla
The Pragmatic Passive
Note: “Casey, the Casual Utilitarian” was removed from the final set. His behaviors and goals overlapped significantly with other personas and didn’t offer unique design implications. Meeting the needs of the four remaining personas would effectively satisfy over 90% of Casey’s needs, making his inclusion strategically redundant.
✺
Deliverables & Impact
✺
The personas were delivered in two formats: a set of persona posters for daily communication, and a standard UX research deck detailing methodology, findings, and design implications. Each profile was built around:
End goals (JTBD-inspired)
Behavior patterns
Pain points and triggers
Technographic context
Quotes and visual storytelling
✺
Product Impact
Design teams used personas to reframe onboarding and feature education, especially for low-confidence users like Vesper and Priscilla.
✺
Marketing Impact
The Petersons and Isaac became central to monetization efforts, as their segments represented the highest purchasing intent and willingness to pay.
✺
Reflection
✺
This project changed how our teams talked about users. It gave everyone deeper empathy and a richer vocabulary to discuss real-world behaviors and needs, not just age or device types.
That said, I do wish I had delivered a complete moment-by-moment journey map to show how each persona engaged with our product over time. While I did follow up with a purchase journey study that supported the marketing team’s strategy, it didn’t fully bridge the gap between discovery and in-product interaction. That’s something I hope to explore more deeply in future foundational research.
If I could improve one thing methodologically, it would be to experiment more with mixed methods for scaling. I conducted all 46 interviews 1:1, which was rich but time-intensive. In hindsight, I could have introduced semi-moderated surveys or remote task probes to capture broader behavioral signals with less overhead—especially to support segmentation validation or quantify fringe needs.
✺
Corporate Persona Update
✺
01 Background
With fewer product launches scheduled for Q4 and newly promoted into the UX Research Manager role, I saw an opportunity to fix this. We needed a fresh, grounded, and scalable set of personas—ones that reflected real behaviors, motivations, and needs across our evolving user base.
02 Challenge
By late 2020, Malwarebytes was no longer just an anti-malware company. We had expanded into privacy protection with the launch of PrivacyVPN, and were in the process of shifting from license key activation to a more seamless, account-based management system, which not only simplifies the purchase flow, but also provides a better user experience for cross platfrom and multi-device usage.
While our products had evolved, our understanding of users had not. The existing consumer personas, created back in 2017, were outdated. They lacked behavioral depth, focused too heavily on buyers rather than users, and failed to reflect users' growing privacy concerns. As a result, the product, design, and marketing teams were operating without a shared, nuanced view of our customers.
Over time, the original personas had been reduced to caricatures: elastic, overly simplified archetypes that no longer served our decision-making needs.
The Director of Product frequently cited his wife’s daycare business, where he played the unofficial IT support role, as justification for designing for "accidental admins."
One PM drew from his own experience supporting his wife’s law firm, which lacked a dedicated IT person and relied on an office manager for tech help.
Even within our own team, the Head of UX referenced her husband managing tech support for their family as an example of why a consumer-grade security experience could scale upward
These personal experiences, while valid in isolation, began to dominate decision-making. As a result, the team doubled down on the narrative that our core users lacked technical proficiency, even in cases where research showed otherwise.
Unpacking this internal bias was critical. The persona update became more than just a research refresh: it was an effort to realign the organization’s mental model of who we were building for, before that misalignment could shape product decisions in risky ways.
While the need for a new corporate persona was clear, the path forward wasn’t simple. We faced several constraints:
Constraints
1.
The existing persona, though still directionally valid, was developed by a former researcher years ago before many of us joined the team. There’s a lack of internal education.
2.
At the time, our core corporate product revamp project was the top priority and a new team had formed to rebuild the console from the ground up. My team was fully allocated on that task.
3.
Recruiting IT admins with security responsibilities—our core audience—was notoriously difficult. A full-scale persona study wasn’t realistic within the timeline.
03 Approach
& Result
By late 2020, Malwarebytes was no longer just an anti-malware company. We had expanded into privacy protection with the launch of PrivacyVPN, and were in the process of shifting from license key activation to a more seamless, account-based management system, which not only simplifies the purchase flow, but also provides a better user experience for cross platfrom and multi-device usage.
While our products had evolved, our understanding of users had not. The existing consumer personas, created back in 2017, were outdated. They lacked behavioral depth, focused too heavily on buyers rather than users, and failed to reflect users' growing privacy concerns. As a result, the product, design, and marketing teams were operating without a shared, nuanced view of our customers.
Over time, the original personas had been reduced to caricatures: elastic, overly simplified archetypes that no longer served our decision-making needs.
87% of participants worked at SMBs (50–2,000 endpoints) with a dedicated IT admin
Most had a bachelor’s degree or higher in Computer Science or a related field
Their average experience was 8+ years in tech roles, many with formal security training
This directly contradicted the internal narrative that our users lacked technical backgrounds.
Using this evidence, we collaboratively updated the existing persona in Miro: commenting on sections to revise, replace, or remove. We also restructured the format based on learnings from the consumer persona redesign, and partnered with our visual designer to give the updated poster a fresh, polished look.
The entire process took just one week, proof that with the right foundation and focused collaboration, meaningful persona work doesn’t always require starting from zero.
04 Impact
The updated persona gave stakeholders a data-backed, up-to-date view of our core IT admin audience—bringing clarity and confidence to the team’s understanding of who we were designing for. The refreshed format also made the persona more accessible and actionable, It’s now being used as a shared communication tool across UX and product teams to align decisions and challenge outdated assumptions.
✺
MSP Persona Update
✺
01 Background
After completing the update for our corporate persona (Masab), it became clear that we also needed to address the Managed Service Provider (MSP) segment.
For context:
Nebula is our platform for direct business customers, where IT admins manage endpoints within their own organization.
OneView is our platform for MSPs, who manage security across multiple client organizations using separate Nebula instances.
While both products serve IT admins, the company context differs significantly. With direct customers, the persona must reflect both the admin and their business environment. With MSPs, that complexity increases—MSPs are managing multiple businesses, often with varying security postures, compliance needs, and operational models.
That said, when it comes to individual product use—monitoring threats, deploying policies, responding to alerts—an IT admin is still an IT admin. Masab remained valid for understanding their day-to-day goals and behaviors
02 Approach
Instead of creating an entirely new persona, I chose to supplement Masab with additional insights specific to MSP companies.
Historically, MSPs had been treated as an add-on to broader product development. As a result, our internal understanding of their business structures, roles, and constraints was limited. I saw this as an opportunity to close that gap.
I conducted 12 in-depth interviews with small to mid-sized MSPs. The goal was to better understand:
Their business models and how they package security services
The composition and expertise of their analyst teams
The security goals of their clients
Their operational challenges in managing cybersecurity at scale
We also updated the firmographic section of Masab to include MSP-specific company traits—building on the same persona framework for consistency.
03 Outcome
The study surfaced new insights about MSPs—many of which had been previously anecdotal or misunderstood. Based on the research, I grouped our target MSPs into three operational categories, each defined by their goals, size, and structural strengths/limitations.
Finally, I created a lightweight MSP supplement persona to pair with Masab—focused not on the individual admin, but on business-level considerations unique to the MSP context. This helped product teams make more informed decisions around licensing models, multi-tenant controls, and report generation features specific to OneView.

© 2025 Alexandra Zhao
Projects
ABOUT
Resume
Connect
Methodology Study
JTBD Framework
UX Researcher
✺
Research Manager
✺
2020 Dec~2023 Mar
✺
02 Personas with Purpose
Building Data- Driven Personas for Consumer and Corporate UX

00 Background
Back in the quiet weeks of December 2020, I finally had time to tackle something long overdue: rebuilding our consumer personas from the ground up. I paused all other research and created four new personas that better reflected our evolving user base, fully replacing the outdated set.
Fast forward two and a half years, and the corporate team was facing a similar need. But this time, we didn’t have the time or resources for a full-scale project. So instead, I led an iterative update as the UX Research Manager, guiding two researchers to refresh the existing personas using insights from recent studies.
Outdated or missing personas are a common challenge in UX research. In this case study, I’ll walk through how I approached both a full rebuild and a thoughtful revision—what worked, what I’d do differently, and lessons you might take into your next persona project.
Let’s begin with the consumer persona project: the ones built from scratch.
Note
I’ve included more detail than I typically would in a case study for fellow UXRs who might be looking for persona inspiration. I learned a lot from reading others and I’d love to give it back to the community.
Some of the extra content is folded by default and you can toggle it open to explore more.
Certain images have been intentionally blurred to respect confidentiality agreements.
Quick Jump
00
Background
01
Consumer Persona Reconstruct
02
Making the Case
03
Methodology Design
04
Research Execution
05
Synthesizing the Data
06
Key Findings
07
Impact
08
Reflection
✺
Consumer Persona Reconstruct
✺
01 Recognizing
the Problem
By late 2020, Malwarebytes was no longer just an anti-malware company. We had expanded into privacy protection with the launch of PrivacyVPN, and were in the process of shifting from license key activation to a more seamless, account-based management system, which not only simplifies the purchase flow, but also provides a better user experience for cross platfrom and multi-device usage.
While our products had evolved, our understanding of users had not. The existing consumer personas, created back in 2017, were outdated. They lacked behavioral depth, focused too heavily on buyers rather than users, and failed to reflect users' growing privacy concerns. As a result, the product, design, and marketing teams were operating without a shared, nuanced view of our customers.
Over time, the original personas had been reduced to caricatures: elastic, overly simplified archetypes that no longer served our decision-making needs.
“Jean-Luc – old and not tech-savvy”
“Ben – young and tech-savvy”
With fewer product launches scheduled for Q4 and newly promoted into the UX Research Manager role, I saw an opportunity to fix this. We needed a fresh, grounded, and scalable set of personas—ones that reflected real behaviors, motivations, and needs across our evolving user base.
02 Making the Case:
Proposal and Stakeholder Buy-In
What Was Broken
Confusion between personas and market segments
Across teams, personas had been reduced to oversimplified stereotypes—“Jean-Luc, old and not tech-savvy” and “Ben, young and tech-savvy.” While memorable, these elastic shorthand characters weren’t grounded in behavioral insight or product goals. They were malleable enough to support some argument but ultimately too vague to guide meaningful design.
No clear user motivations or goals
Scattered behavior patterns
Buyer and user roles were mixed together
Biased sampling
Privacy concerns were barely addressed

I can’t share the 2017 consumer persona example, but you can reference this corporate one. They were created using the same methodology and shared very similar structure.)
What I Would Do Differently
I proposed a hybrid persona framework, grounded in:
Goal-Directed Design (About Face: The Essentials of Interaction Design, by Cooper et al.)
Jobs-to-be-Done (JTBD) theory (When Coffee and Kale Compete, by Alan Klement.)
Ethnographic principles from applied anthropology
The new approach focused less on who users are, and more on what they’re trying to achieve—a better fit for product design and messaging.

(A preview of the new persona format was shared with stakeholders to illustrate the value and usability of the updated approach.)

(The JTBD Data Model shows a process of how new market behavior is created. In this case, it shows how a JTBD is created and how it results in someone hiring solution(s) for it.)
A Clearer Communication Tool
Rather than updating old personas, I started from scratch. The new set would:
Highlight motivations and goals as the centerpiece
Distill clear behavior patterns, not demographic generalizations
Offer practical guidance for design, product, marketing strategies
Result: Stakeholder Buy-In
With strong cross-functional alignment, I dedicated 90% of my time to this foundational initiative while continuing to oversee enterprise research efforts.
Key Research Objectives
Rebuild personas from the ground up
Center on user motivations, goals, and behavior patterns
Deprioritize demographics and buyer-side data
Set the stage for Phase 2: Journey mapping (not covered in this case study)
✺
Planning the Approach
✺
With stakeholder buy-in secured, I moved into the execution of this project. Most of the My goal was to build a persona system grounded in rigorous theory, adaptable across product lifecycles, and usable by cross-functional teams.
03 Methodology Design
The research approach was deliberately layered and collaborative:
1.
Literature Review
Assessed modern persona frameworks, focusing on their application in tech and behavior-driven design.
2.
Product Audit & Heuristic Review
Mapped the current user experience across our consumer product suite to identify behavioral cues and UI gaps.
3.
Stakeholder Interviews
Aligned with cross-functional partners to understand business priorities and clarify scope boundaries.
4.
Iterative Plan Feedback
Presented early drafts of the research plan to design and PM leads, incorporating their feedback to ensure alignment.
5.
Recruitment & Interviews
Conducted remote 1:1 interviews with a diverse set of users, including non-customers, to avoid brand bias.
6.
Analysis & Persona Construction
Synthesized behavioral patterns, underlying goals, and job drivers into actionable personas.
Theoretical Foundations
TL;DR
It’s less about Who they are, and more about how they interact with our product and what they are trying to achieve and most importantly, why does it matter to them.
Theories and principles
This project was guided by a mix of Goal-Directed Design and Jobs-to-be-Done theories, with influences from cognitive psychology and anthropology. These frameworks helped me ask sharper questions, spot behavioral patterns in context, and build personas that were both practical and forward-looking.
Read More
04 Research Execution
Total Participants
46 (U.S. and Canada)
Interview Format
90-minute, 1:1 remote moderated sessions

Interview Design
Each session combined open-ended narrative exploration with a few quantitative prompts to assess:
Security and privacy priorities
Confidence and vulnerability levels
Success criteria for digital security
The core focus was to understand the goals users were trying to achieve, their perceived constraints, and how they navigated their digital lives.
Research Question Guide
1. User Goals & Motivations:
What are they trying to achieve, and why?
2. Behavioral Patterns & Mental Models:
How are they currently navigating digital security?
3. Priorities & Trade-Offs:
How do they rank and justify their preferences?
4. Context of Their Digital Life:What life context shapes their decisions?
05 Synthesizing the Data
A total of 46 sessions were transcribed, coded, and analyzed across four key dimensions:
User goals – What they were trying to achieve
Behavioral patterns – How they approached protection and trade-offs
Mental models – What they believed would keep them safe
Contextual factors – Life stage, device sharing, past experiences
Iterative Clustering
Instead of fitting users into pre-defined archetypes, I took a bottom-up clustering approach to identify groups with shared patterns.
I experimented with different grouping methods—starting with goals, then behaviors, and vice versa—to stress-test the consistency of those patterns.
To supplement the qualitative clusters, I explored basic clustering algorithms using the small-scale quantitative data collected (e.g. vulnerability scores, confidence levels, security vs privacy priorities). Unsurprisingly, the sample size was too small to yield statistically significant clusters, but the data still served as a helpful validation layer to reinforce and challenge the qualitative segmentation.
Common protection goals
Similar logic around trade-offs (free vs paid, simplicity vs control)
Comparable levels of digital confidence and risk tolerance

(snapshot of early analysis: color-coded themes, initial categorization and frequency counts.)


Constructing the Persona Set
The final result was a set of five personas, each anchored by:
A core goal or mental model driving their decisions
A clear set of behavioral tendencies and trade-offs
Emotional and functional success criteria guiding their product expectations
Where relevant, I included overlapping buyer behaviors to support marketing and support team alignment, while ensuring the personas remained focused on in-product user needs.
✺
Key Findings & Personas
✺
06 Key Findings
✺
Security is shifting from device-first to human-first.
Users are thinking less about protecting devices and more about protecting themselves and their families.
✺
Privacy concerns are rising—but confidence remains low.
While users are increasingly aware of privacy risks, many feel ill-equipped to manage them.
✺
Desire for simplicity, transparency, and integration.
All-in-one tools are appealing—but only if they’re easy to use and clearly communicate what’s happening behind the scenes.
✺
Password managers are common but misunderstood.
Many rely on them daily, yet few fully understand how they work—or trust them completely.
✺
Brand trust is fragile.
Loyalty is not guaranteed; users expect ongoing relevance and clear value to stick around.
Quantitative Highlights
1.
89% of participants prioritized identity theft protection as a top need.
2.
Privacy vulnerability was significantly higher than security vulnerability:
44% felt fairly or completely vulnerable about privacy risks (vs. 13% for security).
3.
Confidence in managing privacy was markedly lower than security:
Only 31% felt fairly or completely confident in managing privacy risks, compared to 65% for security.


Final Personas
Vesper
The Vulnerable Senior
The Petersons
Protective Parents (treated as a joint decision-making unit)
Issac
The Informed Power User
Priscilla
The Pragmatic Passive
Note: “Casey, the Casual Utilitarian” was removed from the final set. His behaviors and goals overlapped significantly with other personas and didn’t offer unique design implications. Meeting the needs of the four remaining personas would effectively satisfy over 90% of Casey’s needs, making his inclusion strategically redundant.
✺
Deliverables & Impact
✺
The personas were delivered in two formats: a set of persona posters for daily communication, and a standard UX research deck detailing methodology, findings, and design implications. Each profile was built around:
End goals (JTBD-inspired)
Behavior patterns
Pain points and triggers
Technographic context
Quotes and visual storytelling
✺
Product Impact
Design teams used personas to reframe onboarding and feature education, especially for low-confidence users like Vesper and Priscilla.
✺
Marketing Impact
The Petersons and Isaac became central to monetization efforts, as their segments represented the highest purchasing intent and willingness to pay.
✺
Reflection
✺
This project changed how our teams talked about users. It gave everyone deeper empathy and a richer vocabulary to discuss real-world behaviors and needs, not just age or device types.
That said, I do wish I had delivered a complete moment-by-moment journey map to show how each persona engaged with our product over time. While I did follow up with a purchase journey study that supported the marketing team’s strategy, it didn’t fully bridge the gap between discovery and in-product interaction. That’s something I hope to explore more deeply in future foundational research.
If I could improve one thing methodologically, it would be to experiment more with mixed methods for scaling. I conducted all 46 interviews 1:1, which was rich but time-intensive. In hindsight, I could have introduced semi-moderated surveys or remote task probes to capture broader behavioral signals with less overhead—especially to support segmentation validation or quantify fringe needs.
✺
Corporate Persona Update
✺
01 Background
With fewer product launches scheduled for Q4 and newly promoted into the UX Research Manager role, I saw an opportunity to fix this. We needed a fresh, grounded, and scalable set of personas—ones that reflected real behaviors, motivations, and needs across our evolving user base.
02 Challenge
By late 2020, Malwarebytes was no longer just an anti-malware company. We had expanded into privacy protection with the launch of PrivacyVPN, and were in the process of shifting from license key activation to a more seamless, account-based management system, which not only simplifies the purchase flow, but also provides a better user experience for cross platfrom and multi-device usage.
While our products had evolved, our understanding of users had not. The existing consumer personas, created back in 2017, were outdated. They lacked behavioral depth, focused too heavily on buyers rather than users, and failed to reflect users' growing privacy concerns. As a result, the product, design, and marketing teams were operating without a shared, nuanced view of our customers.
Over time, the original personas had been reduced to caricatures: elastic, overly simplified archetypes that no longer served our decision-making needs.
The Director of Product frequently cited his wife’s daycare business, where he played the unofficial IT support role, as justification for designing for "accidental admins."
One PM drew from his own experience supporting his wife’s law firm, which lacked a dedicated IT person and relied on an office manager for tech help.
Even within our own team, the Head of UX referenced her husband managing tech support for their family as an example of why a consumer-grade security experience could scale upward
These personal experiences, while valid in isolation, began to dominate decision-making. As a result, the team doubled down on the narrative that our core users lacked technical proficiency, even in cases where research showed otherwise.
Unpacking this internal bias was critical. The persona update became more than just a research refresh: it was an effort to realign the organization’s mental model of who we were building for, before that misalignment could shape product decisions in risky ways.
Constraints
While the need for a new corporate persona was clear, the path forward wasn’t simple. We faced several constraints:
1.
The existing persona, though still directionally valid, was developed by a former researcher years ago before many of us joined the team. There’s a lack of internal education.
2.
At the time, our core corporate product revamp project was the top priority and a new team had formed to rebuild the console from the ground up. My team was fully allocated on that task.
3.
Recruiting IT admins with security responsibilities—our core audience—was notoriously difficult. A full-scale persona study wasn’t realistic within the timeline.
03 Approach
& Result
By late 2020, Malwarebytes was no longer just an anti-malware company. We had expanded into privacy protection with the launch of PrivacyVPN, and were in the process of shifting from license key activation to a more seamless, account-based management system, which not only simplifies the purchase flow, but also provides a better user experience for cross platfrom and multi-device usage.
While our products had evolved, our understanding of users had not. The existing consumer personas, created back in 2017, were outdated. They lacked behavioral depth, focused too heavily on buyers rather than users, and failed to reflect users' growing privacy concerns. As a result, the product, design, and marketing teams were operating without a shared, nuanced view of our customers.
Over time, the original personas had been reduced to caricatures: elastic, overly simplified archetypes that no longer served our decision-making needs.
87% of participants worked at SMBs (50–2,000 endpoints) with a dedicated IT admin
Most had a bachelor’s degree or higher in Computer Science or a related field
Their average experience was 8+ years in tech roles, many with formal security training
This directly contradicted the internal narrative that our users lacked technical backgrounds.
Using this evidence, we collaboratively updated the existing persona in Miro: commenting on sections to revise, replace, or remove. We also restructured the format based on learnings from the consumer persona redesign, and partnered with our visual designer to give the updated poster a fresh, polished look.
The entire process took just one week, proof that with the right foundation and focused collaboration, meaningful persona work doesn’t always require starting from zero.
04 Impact
The updated persona gave stakeholders a data-backed, up-to-date view of our core IT admin audience—bringing clarity and confidence to the team’s understanding of who we were designing for. The refreshed format also made the persona more accessible and actionable, It’s now being used as a shared communication tool across UX and product teams to align decisions and challenge outdated assumptions.
✺
MSP Persona Update
✺
01 Background
After completing the update for our corporate persona (Masab), it became clear that we also needed to address the Managed Service Provider (MSP) segment.
For context:
Nebula is our platform for direct business customers, where IT admins manage endpoints within their own organization.
OneView is our platform for MSPs, who manage security across multiple client organizations using separate Nebula instances.
While both products serve IT admins, the company context differs significantly. With direct customers, the persona must reflect both the admin and their business environment. With MSPs, that complexity increases—MSPs are managing multiple businesses, often with varying security postures, compliance needs, and operational models.
That said, when it comes to individual product use—monitoring threats, deploying policies, responding to alerts—an IT admin is still an IT admin. Masab remained valid for understanding their day-to-day goals and behaviors
02 Approach
Instead of creating an entirely new persona, I chose to supplement Masab with additional insights specific to MSP companies.
Historically, MSPs had been treated as an add-on to broader product development. As a result, our internal understanding of their business structures, roles, and constraints was limited. I saw this as an opportunity to close that gap.
I conducted 12 in-depth interviews with small to mid-sized MSPs. The goal was to better understand:
Their business models and how they package security services
The composition and expertise of their analyst teams
The security goals of their clients
Their operational challenges in managing cybersecurity at scale
We also updated the firmographic section of Masab to include MSP-specific company traits—building on the same persona framework for consistency.
03 Outcome
The study surfaced new insights about MSPs—many of which had been previously anecdotal or misunderstood. Based on the research, I grouped our target MSPs into three operational categories, each defined by their goals, size, and structural strengths/limitations.
Finally, I created a lightweight MSP supplement persona to pair with Masab—focused not on the individual admin, but on business-level considerations unique to the MSP context. This helped product teams make more informed decisions around licensing models, multi-tenant controls, and report generation features specific to OneView.

© 2025 Alexandra Zhao
Projects
ABOUT
Resume
Connect
Quick Jump
00
Background
01
Consumer Persona Reconstruct
02
Making the Case
03
Methodology Design
04
Research Execution
05
Synthesizing the Data
06
Key Findings
07
Impact
08
Reflection
Previous Study
Next Study
Methodology Study
JTBD Framework
UX Researcher
✺
Research Manager
✺
2020 Dec~2023 Mar
✺
02 Personas with Purpose
Building Data- Driven Personas for Consumer and Corporate UX

00 Background
Back in the quiet weeks of December 2020, I finally had time to tackle something long overdue: rebuilding our consumer personas from the ground up. I paused all other research and created four new personas that better reflected our evolving user base, fully replacing the outdated set.
Fast forward two and a half years, and the corporate team was facing a similar need. But this time, we didn’t have the time or resources for a full-scale project. So instead, I led an iterative update as the UX Research Manager, guiding two researchers to refresh the existing personas using insights from recent studies.
Outdated or missing personas are a common challenge in UX research. In this case study, I’ll walk through how I approached both a full rebuild and a thoughtful revision—what worked, what I’d do differently, and lessons you might take into your next persona project.
Let’s begin with the consumer persona project: the ones built from scratch.
Note
I’ve included more detail than I typically would in a case study for fellow UXRs who might be looking for persona inspiration. I learned a lot from reading others and I’d love to give it back to the community.
Some of the extra content is folded by default and you can toggle it open to explore more.
Certain images have been intentionally blurred to respect confidentiality agreements.
Quick Jump
00
Background
01
Consumer Persona Reconstruct
02
Making the Case
03
Methodology Design
04
Research Execution
05
Synthesizing the Data
06
Key Findings
07
Impact
08
Reflection
✺
Consumer Persona Reconstruct
✺
01 Recognizing
the Problem
By late 2020, Malwarebytes was no longer just an anti-malware company. We had expanded into privacy protection with the launch of PrivacyVPN, and were in the process of shifting from license key activation to a more seamless, account-based management system, which not only simplifies the purchase flow, but also provides a better user experience for cross platform and multi-device usage.
While our products had evolved, our understanding of users had not. The existing consumer personas, created back in 2017, were outdated. They lacked behavioral depth, focused too heavily on buyers rather than users, and failed to reflect users' growing privacy concerns. As a result, the product, design, and marketing teams were operating without a shared, nuanced view of our customers.
Over time, the original personas had been reduced to caricatures: elastic, overly simplified archetypes that no longer served our decision-making needs.
“Jean-Luc – old and not tech-savvy”
“Ben – young and tech-savvy”
With fewer product launches scheduled for Q4 and newly promoted into the UX Research Manager role, I saw an opportunity to fix this. We needed a fresh, grounded, and scalable set of personas—ones that reflected real behaviors, motivations, and needs across our evolving user base.
02 Making the Case:
Proposal and Stakeholder Buy-In
What Was Broken
Confusion between personas and market segments
Across teams, personas had been reduced to oversimplified stereotypes—“Jean-Luc, old and not tech-savvy” and “Ben, young and tech-savvy.” While memorable, these elastic shorthand characters weren’t grounded in behavioral insight or product goals. They were malleable enough to support some argument but ultimately too vague to guide meaningful design.
No clear user motivations or goals
Scattered behavior patterns
Buyer and user roles were mixed together
Biased sampling
Privacy concerns were barely addressed

I can’t share the 2017 consumer persona example, but you can reference this corporate one. They were created using the same methodology and shared very similar structure.)
What I Would Do Differently
I proposed a hybrid persona framework, grounded in:
Goal-Directed Design (About Face: The Essentials of Interaction Design, by Cooper et al.)
Jobs-to-be-Done (JTBD) theory (When Coffee and Kale Compete, by Alan Klement.)
Ethnographic principles from applied anthropology
The new approach focused less on who users are, and more on what they’re trying to achieve—a better fit for product design and messaging.

(A preview of the new persona format was shared with stakeholders to illustrate the value and usability of the updated approach.)

(The JTBD Data Model shows a process of how new market behavior is created. In this case, it shows how a JTBD is created and how it results in someone hiring solution(s) for it.)
A Clearer Communication Tool
Rather than updating old personas, I started from scratch. The new set would:
Highlight motivations and goals as the centerpiece
Distill clear behavior patterns, not demographic generalizations
Offer practical guidance for design, product, marketing strategies
Result: Stakeholder Buy-In
With strong cross-functional alignment, I dedicated 90% of my time to this foundational initiative while continuing to oversee enterprise research efforts.
Key Research Objectives
Rebuild personas from the ground up
Center on user motivations, goals, and behavior patterns
Deprioritize demographics and buyer-side data
Set the stage for Phase 2: Journey mapping (not covered in this case study)
✺
Planning the Approach
✺
With stakeholder buy-in secured, I moved into the execution of this project. Most of the My goal was to build a persona system grounded in rigorous theory, adaptable across product lifecycles, and usable by cross-functional teams.
03 Methodology Design
The research approach was deliberately layered and collaborative:
1.
Literature Review
Assessed modern persona frameworks, focusing on their application in tech and behavior-driven design.
2.
Product Audit & Heuristic Review
Mapped the current user experience across our consumer product suite to identify behavioral cues and UI gaps.
3.
Stakeholder Interviews
Aligned with cross-functional partners to understand business priorities and clarify scope boundaries.
4.
Iterative Plan Feedback
Presented early drafts of the research plan to design and PM leads, incorporating their feedback to ensure alignment.
5.
Recruitment & Interviews
Conducted remote 1:1 interviews with a diverse set of users, including non-customers, to avoid brand bias.
6.
Analysis & Persona Construction
Synthesized behavioral patterns, underlying goals, and job drivers into actionable personas.
Theoretical Foundations
TL;DR
It’s less about Who they are, and more about how they interact with our product and what they are trying to achieve and most importantly, why does it matter to them.
Theories and principles
This project was guided by a mix of Goal-Directed Design and Jobs-to-be-Done theories, with influences from cognitive psychology and anthropology. These frameworks helped me ask sharper questions, spot behavioral patterns in context, and build personas that were both practical and forward-looking.
Read More
04 Research Execution
Total Participants
46 (U.S. and Canada)
Interview Format
90-minute, 1:1 remote moderated sessions

Interview Design
Each session combined open-ended narrative exploration with a few quantitative prompts to assess:
Security and privacy priorities
Confidence and vulnerability levels
Success criteria for digital security
The core focus was to understand the goals users were trying to achieve, their perceived constraints, and how they navigated their digital lives.
Research Question Guide
1. User Goals & Motivations:
What are they trying to achieve, and why?
2. Behavioral Patterns & Mental Models:
How are they currently navigating digital security?
3. Priorities & Trade-Offs:
How do they rank and justify their preferences?
4. Context of Their Digital Life:What life context shapes their decisions?
05 Synthesizing the Data
A total of 46 sessions were transcribed, coded, and analyzed across four key dimensions:
User goals – What they were trying to achieve
Behavioral patterns – How they approached protection and trade-offs
Mental models – What they believed would keep them safe
Contextual factors – Life stage, device sharing, past experiences
Iterative Clustering
Instead of fitting users into pre-defined archetypes, I took a bottom-up clustering approach to identify groups with shared patterns.
I experimented with different grouping methods, starting with goals, then behaviors, and vice versa, to stress-test the consistency of those patterns.
Common protection goals
Similar logic around trade-offs (free vs paid, simplicity vs control)
Comparable levels of digital confidence and risk tolerance
To supplement the qualitative clusters, I explored basic clustering algorithms using the small-scale quantitative data collected (e.g. vulnerability scores, confidence levels, security vs privacy priorities). Unsurprisingly, the sample size was too small to yield statistically significant clusters, but the data still served as a helpful validation layer to reinforce and challenge the qualitative segmentation.

(snapshot of early analysis: color-coded themes, initial categorization and frequency counts.)


Constructing the Persona Set
The final result was a set of five personas, each anchored by:
A core goal or mental model driving their decisions
A clear set of behavioral tendencies and trade-offs
Emotional and functional success criteria guiding their product expectations
Where relevant, I included buyer side behaviors to support our marketing and support team, while keeping the primary focus on in-product user needs.
✺
Key Findings & Personas
✺
06 Key Findings
✺
Security is shifting from device-first to human-first.
Users are thinking less about protecting devices and more about protecting themselves and their families.
✺
Privacy concerns are rising—but confidence remains low.
While users are increasingly aware of privacy risks, many feel ill-equipped to manage them.
✺
Desire for simplicity, transparency, and integration.
All-in-one tools are appealing—but only if they’re easy to use and clearly communicate what’s happening behind the scenes.
✺
Password managers are common but misunderstood.
Many rely on them daily, yet few fully understand how they work—or trust them completely.
✺
Brand trust is fragile.
Loyalty is not guaranteed; users expect ongoing relevance and clear value to stick around.
Quantitative Highlights
1.
89% of participants prioritized identity theft protection as a top need.
2.
Privacy vulnerability was significantly higher than security vulnerability:
44% felt fairly or completely vulnerable about privacy risks (vs. 13% for security).
3.
Confidence in managing privacy was markedly lower than security:
Only 31% felt fairly or completely confident in managing privacy risks, compared to 65% for security.


Final Personas
Vesper
The Vulnerable Senior
The Petersons
Protective Parents (treated as a joint decision-making unit)
Issac
The Informed Power User
Priscilla
The Pragmatic Passive
Note: “Casey, the Casual Utilitarian” was removed from the final set. His behaviors and goals overlapped significantly with other personas and didn’t offer unique design implications. Meeting the needs of the four remaining personas would effectively satisfy over 90% of Casey’s needs, making his inclusion strategically redundant.
✺
Deliverables & Impact
✺
The personas were delivered in two formats: a set of persona posters for daily communication, and a standard UX research deck detailing methodology, findings, and design implications. Each profile was built around:
End goals (JTBD-inspired)
Behavior patterns
Pain points and triggers
Technographic context
Quotes and visual storytelling
✺
Product Impact
Design teams used personas to reframe onboarding and feature education, especially for low-confidence users like Vesper and Priscilla.
✺
Marketing Impact
The Petersons and Isaac became central to monetization efforts, as their segments represented the highest purchasing intent and willingness to pay.
✺
Reflection
✺
This project changed how our teams talked about users. It gave everyone deeper empathy and a richer vocabulary to discuss real-world behaviors and needs, not just age or device types.
That said, I do wish I had delivered a complete moment-by-moment journey map to show how each persona engaged with our product over time. While I did follow up with a purchase journey study that supported the marketing team’s strategy, it didn’t fully bridge the gap between discovery and in-product interaction. That’s something I hope to explore more deeply in future foundational research.
If I could improve one thing methodologically, it would be to experiment more with mixed methods for scaling. I conducted all 46 interviews 1:1, which was rich but time-intensive. In hindsight, I could have introduced semi-moderated surveys or remote task probes to capture broader behavioral signals with less overhead—especially to support segmentation validation or quantify fringe needs.
✺
Corporate Persona Update
✺
01 Background
The need for a persona update became clear during the transition from Project Flywheel to SAM. As we rebuilt our core product experience, product leadership began reinforcing the idea that our primary users were “non-technical admins”—individuals without formal IT backgrounds who needed a product that was simple enough for anyone to use. While this framing made sense during the Flywheel phase, especially when exploring an unified, accessible design system, it became limiting and potentially harmful when carried into the more security-focused rebuild of Nebula. With fewer product launches scheduled for Q4 , I saw an opportunity to fix this.
02 Challenge
One of the biggest challenges in updating the personas was overcoming deep-seated internal bias, often shaped by personal anecdotes.
The Director of Product frequently cited his wife’s daycare business, where he played the unofficial IT support role, as justification for designing for "accidental admins."
One PM drew from his own experience supporting his wife’s law firm, which lacked a dedicated IT person and relied on an office manager for tech help.
Even within our own team, the Head of UX referenced her husband managing tech support for their family as an example of why a consumer-grade security experience could scale upward
These personal experiences, while valid in isolation, began to dominate decision-making. As a result, the team doubled down on the narrative that our core users lacked technical proficiency, even in cases where research showed otherwise.
Unpacking this internal bias was critical. The persona update became more than just a research refresh: it was an effort to realign the organization’s mental model of who we were building for, before that misalignment could shape product decisions in risky ways.
Constraints
While the need for a new corporate persona was clear, the path forward wasn’t simple. We faced several constraints:
1.
The existing persona, though still directionally valid, was developed by a former researcher years ago before many of us joined the team. There’s a lack of internal education.
2.
At the time, our core corporate product revamp project was the top priority and a new team had formed to rebuild the console from the ground up. My team was fully allocated on that task.
3.
Recruiting IT admins with security responsibilities—our core audience—was notoriously difficult. A full-scale persona study wasn’t realistic within the timeline.
03 Approach
& Result
Instead of starting from scratch, I proposed a rapid persona refresh using existing insights from the previous 12 months of research.
Over the past year, our team had interviewed more than 100 IT admins across projects. While these interviews were originally conducted for other initiatives, they represented a goldmine of behavioral and demographic data. Together with two senior UX researchers, we mined this data to answer the core question at the heart of the debate: Who are our users, really?
The results were striking:
87% of participants worked at SMBs (50–2,000 endpoints) with a dedicated IT admin
Most had a bachelor’s degree or higher in Computer Science or a related field
Their average experience was 8+ years in tech roles, many with formal security training
This directly contradicted the internal narrative that our users lacked technical backgrounds.
Using this evidence, we collaboratively updated the existing persona in Miro: commenting on sections to revise, replace, or remove. We also restructured the format based on learnings from the consumer persona redesign, and partnered with our visual designer to give the updated poster a fresh, polished look.
The entire process took just one week, proof that with the right foundation and focused collaboration, meaningful persona work doesn’t always require starting from zero.
04 Impact
The updated persona gave stakeholders a data-backed, up-to-date view of our core IT admin audience—bringing clarity and confidence to the team’s understanding of who we were designing for. The refreshed format also made the persona more accessible and actionable, It’s now being used as a shared communication tool across UX and product teams to align decisions and challenge outdated assumptions.
✺
MSP Persona Update
✺
01 Background
After completing the update for our corporate persona (Masab), it became clear that we also needed to address the Managed Service Provider (MSP) segment.
For context:
Nebula is our platform for direct business customers, where IT admins manage endpoints within their own organization.
OneView is our platform for MSPs, who manage security across multiple client organizations using separate Nebula instances.
While both products serve IT admins, the company context differs significantly. With direct customers, the persona must reflect both the admin and their business environment. With MSPs, that complexity increases—MSPs are managing multiple businesses, often with varying security postures, compliance needs, and operational models.
That said, when it comes to individual product use—monitoring threats, deploying policies, responding to alerts—an IT admin is still an IT admin. Masab remained valid for understanding their day-to-day goals and behaviors
02 Approach
Instead of creating an entirely new persona, I chose to supplement Masab with additional insights specific to MSP companies.
Historically, MSPs had been treated as an add-on to broader product development. As a result, our internal understanding of their business structures, roles, and constraints was limited. I saw this as an opportunity to close that gap.
I conducted 12 in-depth interviews with small to mid-sized MSPs. The goal was to better understand:
Their business models and how they package security services
The composition and expertise of their analyst teams
The security goals of their clients
Their operational challenges in managing cybersecurity at scale
We also updated the firmographic section of Masab to include MSP-specific company traits—building on the same persona framework for consistency.
03 Outcome
The study surfaced new insights about MSPs—many of which had been previously anecdotal or misunderstood. Based on the research, I grouped our target MSPs into three operational categories, each defined by their goals, size, and structural strengths/limitations.
Finally, I created a lightweight MSP supplement persona to pair with Masab—focused not on the individual admin, but on business-level considerations unique to the MSP context. This helped product teams make more informed decisions around licensing models, multi-tenant controls, and report generation features specific to OneView.

© 2025 Alexandra Zhao